Nordea's netbank - outdated and insecure...
I hold a Finnish identity card with strong authentication certificate (FINeID). The FINeID website states, this card could also be used for online banking, so I contacted my bank Nordea and asked how to do that. The first answer was a mile long copy-paste text about the FINeID card which was no clear answer to my question, so I asked again and received the information that Nordea Finland offers any kind of card authentication only for business customers. After I pointed out that the current code system is obsolete and insecure and that I used HBCI cards for online banking in Germany already 10 years before I moved to Finland, the customer service replied that Nordea’s netbank code system was old-fashioned but quite secure.
Well, let’s have a look at how secure the system really is…
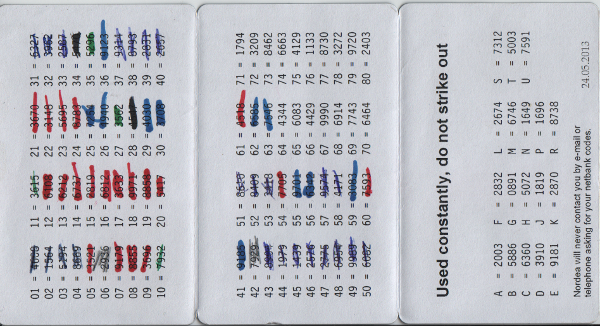
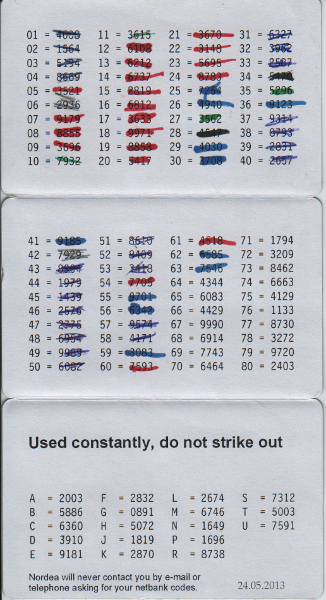
To be able to use Nordea’s netbank, you need 3 codes. A user identification code (8 digits), a one-time code and a verification code (both 4 digits). The user ID is sent to the user in a separate letter, doesn’t change and should be stored separately from the code card. The one-time codes and confirmation codes are on a code card (see image to the right) which is also sent via letter.
The authentication process works so that to login into netbank, the user enters their user ID and the next unused one-time password. After login, transactions are authenticated with the verification codes. Those transaction authentication can be also used in bulk, i.e., not every transaction needs to be authenticated separately.
Now, why is that insecure, you might ask. 3 different codes seem reasonable secure?
Well, first of all, each and every system where the user enters a code via the PC keyboard has to be considered insecure. For well more than 15 years, viruses and trojans have been found in the wild which are specialized in intercepting codes for online banking. This attack software is developed by specialists and rented or sold to criminal organisations. In the simplest case, it will hook itself inside the user’s web browser and when a user enters e.g. a money transfer and enters the verification code, the attack-software will intercept and hold this data and replace the destination data which the user entered with it’s own - using the transaction verification code the user just provided. German banks have run a race over the last 15 or so years, trying to improve the system, inventing new systems, where e.g. the verification code is sent to the user’s mobile phone by SMS, just to find new versions of the attack-software shortly later which coped with the new invention.
Again: Each and every system where the user enters any kind of code via the PC keyboard is inherently insecure. Not “but”, “if”, “when”, … It’s insecure, basta!
Now, Nordea’s system is about as insecure as one can possibly make a code system…
- The one-time codes are used in linear sequence and struck out on the card, making it very easy to guess which code to use if someone steals the card.
- The one-time codes are only used for login into netbank - transaction verification is not done with one-time codes.
- The verification codes are reused! And there’s only 18 of them! Means, after just a few times of keylogging the user’s netbank sessions, any attack-software would have a very fair chance that a verification code, which is already known to it, is requested by netbank, which means, it only needs to hijack the open session from the browser and can start making transactions as it likes.
It’s almost inconceivable that any bank nowadays still uses printed code lists but the fact that Nordea doesn’t even offer any kind of authentication card solution for private customers at all is beyond any justification. This kind of “well, let’s hope, it doesn’t hit us”-attitude has cost countless customers in Germany and other countries thousands of Euros in damages and one should expect that a huge international bank like Nordea would be able to learn from the mistakes, others have made in the past.
And it is simply a fact that currently, the only secure way of authenticating logins and transactions is by means of a an external cryptographic device which has it’s own keypad for code entry - such as a cardreader with a PKCS#11, PKCS#15, ISO/IEC 7816-15 or an HBCI/FinTS card.